As we delve deeper into the world of network packets, it’s essential to recognize their role in various applications and services that we use daily. From sending emails to streaming videos, network packets are the unseen facilitators of our digital interactions. They allow for the efficient transfer of data, ensuring that information reaches its destination quickly and accurately. This guide aims to provide a comprehensive understanding of network packets, making it accessible to both beginners and those with a technical background.
What are Packets?
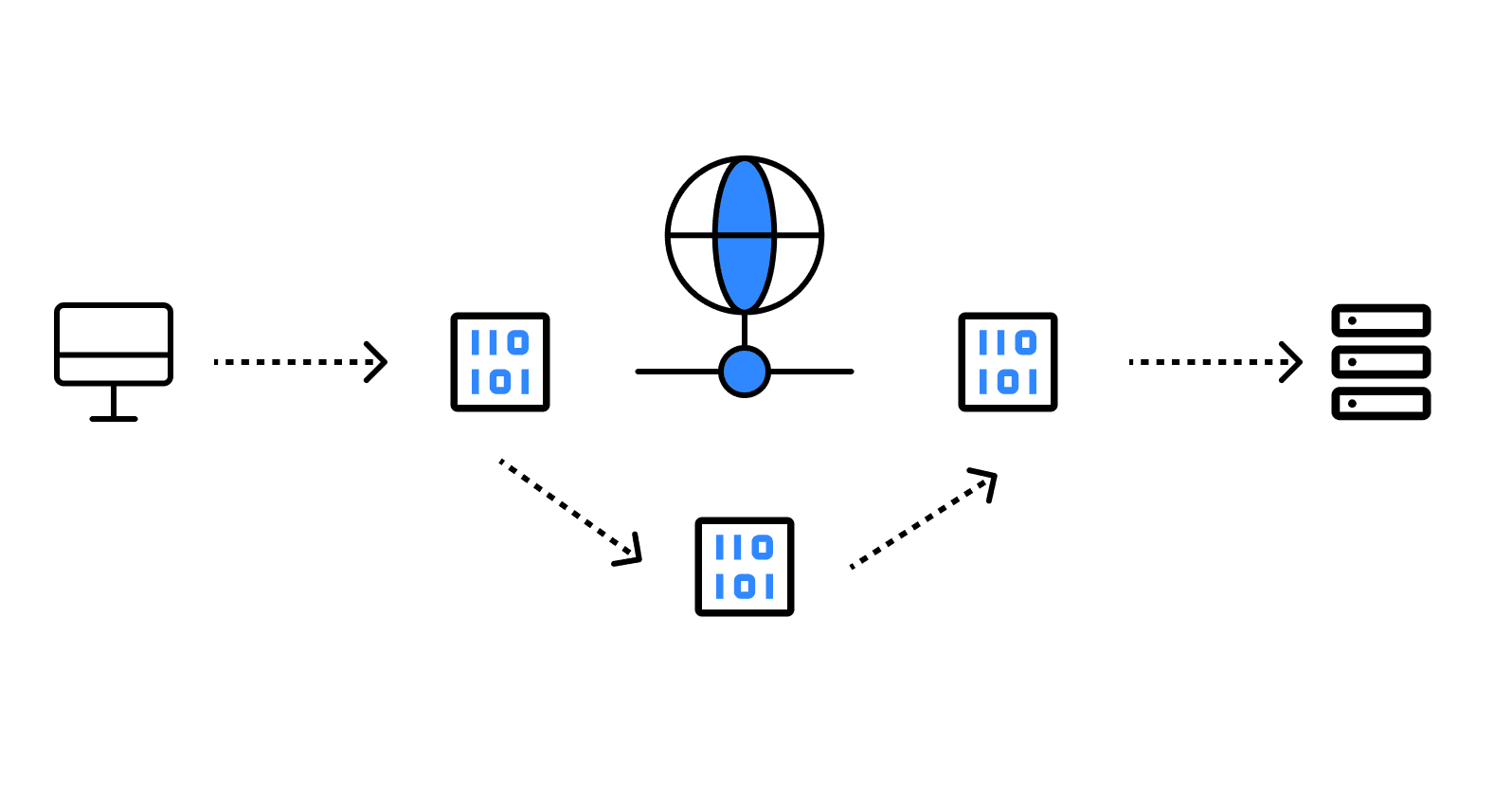
Packets are small units of data that are transmitted over a network. When information is sent from one device to another, it is broken down into manageable pieces called packets. Each packet contains not only a portion of the actual data being transmitted (known as the payload) but also essential metadata in the form of headers and sometimes trailers. This metadata includes information such as the source and destination IP addresses, sequence numbers, and error-checking data, which help ensure that the packets are delivered correctly and in the right order.
Why are Packets Important?
- Efficient Data Transmission: By breaking down large amounts of data into smaller packets, networks can transmit information more efficiently. This allows for better use of bandwidth and reduces the likelihood of congestion.
- Error Detection and Correction: Packets include error-checking information, which helps detect and correct errors that may occur during transmission. This ensures data integrity and reliability, which are crucial for applications like file transfers and online communications.
- Routing and Delivery: Packets can take different paths through a network to reach their destination. Routers use the information in the packet headers to determine the best route, allowing for dynamic and efficient data delivery even in complex networks.
- Support for Multiple Applications: Different types of packets (such as TCP, UDP, and ICMP) support various applications and services. This versatility allows for a wide range of functionalities, from web browsing and email to real-time video streaming and online gaming.
- Scalability: The packet-switching method allows networks to scale easily. As more devices connect to the network, packets can be routed independently, accommodating increased traffic without requiring a complete overhaul of the network infrastructure.
- Security: Packets can be encrypted to protect sensitive information during transmission. This is particularly important in today’s digital landscape, where data breaches and cyber threats are prevalent.
Packets are fundamental to modern networking. They enable efficient, reliable, and secure communication across diverse applications and devices, making them a critical component of the internet and other networks.
Anatomy of a Network Packets
Understanding the anatomy of a network packet is crucial for grasping how data is transmitted across networks. Each component of a packet plays a vital role in ensuring that data is delivered correctly and efficiently.
1. Packet Structure
- Header: The header is not just a simple label; it contains critical information that dictates how the packet should be handled. For instance, the header may include flags that indicate whether the packet is part of a larger data stream or if it requires acknowledgment from the receiving device.
- Payload: The payload is the heart of the packet, containing the actual data being transmitted. This could range from a small text message to a large multimedia file. The size of the payload can vary significantly depending on the application and the type of data being sent.
- Trailer/Footer: The trailer often includes a checksum or hash value that helps verify the integrity of the packet. When the packet reaches its destination, the receiving device can use this information to check for errors that may have occurred during transmission.
2. Key Components of a Packet Header
Understanding the key components of a packet header is essential for troubleshooting network issues and optimizing performance.
- Source IP Address: This address is crucial for routing the packet back to the sender. It allows the receiving device to send responses or acknowledgments back to the original source.
- Destination IP Address: The destination IP address is vital for ensuring that the packet reaches the correct endpoint. Routers use this information to determine the best path for the packet to travel through the network.
- Protocol Information: The protocol information in the header indicates how the packet should be processed. For example, if the packet is a TCP packet, the receiving device will know to establish a connection and ensure reliable delivery.
- Packet Sequence Number: This number is particularly important for protocols like TCP, where packets may arrive out of order. The sequence number allows the receiving device to reorder the packets correctly.
- Time to Live (TTL): The TTL value is decremented by each router that processes the packet. If the TTL reaches zero, the packet is discarded, preventing it from circulating indefinitely in the network.
Types of Network Packets
Each type of network packet serves a specific purpose, and understanding these differences is key to effective network management.
- TCP Packets: TCP packets are designed for reliability. They establish a connection between the sender and receiver before data transmission begins, ensuring that all packets are received and in the correct order. This is achieved through a process known as the TCP handshake, which involves three steps: SYN, SYN-ACK, and ACK. This process establishes a reliable connection, making TCP ideal for applications where data integrity is paramount, such as file transfers and web browsing.
- UDP Packets: UDP packets, on the other hand, are used for applications where speed is more critical than reliability. They do not establish a connection before sending data, which allows for faster transmission. However, this means that there is no guarantee that packets will arrive at their destination or that they will arrive in the correct order. This makes UDP suitable for real-time applications like online gaming and video conferencing, where a few lost packets do not significantly impact the overall experience.
- ICMP Packets: ICMP packets are primarily used for network diagnostics and error reporting. They help network administrators troubleshoot connectivity issues and monitor network performance. For example, the "ping" command uses ICMP packets to check the reachability of a host on a network, providing valuable information about latency and packet loss.
- IP Packets: IP packets are the fundamental units of data that are routed across networks. They can be encapsulated within other protocols, such as TCP or UDP, allowing for flexible communication methods. Understanding IP packets is essential for anyone working with networking, as they form the basis of how data is transmitted over the internet.
- Ethernet Packets: Ethernet packets are used in local area networks (LANs) and are defined by the Ethernet protocol. They encapsulate IP packets and are essential for communication within a network. Ethernet packets include additional information, such as the MAC (Media Access Control) addresses of the sender and receiver, which helps ensure that data is delivered to the correct device within a local network.
Packets Transmission Process
The packet transmission process is a complex series of steps that ensures data is sent and received accurately.
- Packet Switching: Packet switching allows multiple packets from different sources to share the same network resources. This method is more efficient than traditional circuit-switching methods, where a dedicated path is established for each communication session. Packet switching enables dynamic routing, allowing packets to take different paths to their destination based on current network conditions.
- Routing: Routing is a critical function in packet transmission. Routers use routing tables to determine the best path for packets based on various factors, including network congestion, link reliability, and the number of hops to the destination. Advanced routing protocols, such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol), help optimize the routing process, ensuring efficient data delivery.
- Fragmentation and Reassembly: Fragmentation occurs when packets exceed the maximum transmission unit (MTU) of a network segment. In such cases, the packet is divided into smaller fragments, each of which is sent separately. The receiving device is responsible for reassembling these fragments into the original packet. This process is crucial for maintaining data integrity, especially in networks with varying MTU sizes.
- Error Checking and Correction: Error checking and correction mechanisms are essential for ensuring data integrity during transmission. Common techniques include checksums, cyclic redundancy checks (CRC), and automatic repeat requests (ARQ). These methods help detect and correct errors that may occur due to noise, interference, or other factors affecting the transmission medium.
Packets Communication Protocols
Understanding packet communication protocols is vital for anyone involved in networking.
- TCP/IP Protocol Suite: The TCP/IP protocol suite is a set of communication protocols used for the internet and similar networks. It consists of several layers, each responsible for different aspects of data transmission. The suite includes protocols for application layer communication (HTTP, FTP), transport layer reliability (TCP, UDP), and network layer addressing (IP).
- OSI Model and Packet Transmission: The OSI model provides a framework for understanding how different networking protocols interact. Each layer of the OSI model serves a specific function, from physical transmission of data to application-level interactions. Understanding the OSI model helps network professionals troubleshoot issues and design efficient networks.
- Packet Encapsulation: Packet encapsulation is a crucial process that allows data to be transmitted across different network layers. Each layer adds its own header to the packet, providing the necessary information for that layer's specific function. This encapsulation process enables interoperability between different protocols and devices, ensuring seamless communication across diverse networks.
Network Packets Security
As cyber threats continue to evolve, securing network packets is more important than ever.
- Packet Sniffing: Packet sniffing tools can be used for both legitimate and malicious purposes. Network administrators often use sniffers to monitor traffic and troubleshoot issues, while attackers may use them to capture sensitive information. To mitigate the risks associated with packet sniffing, organizations should implement strong encryption protocols and secure network configurations.
- Packet Filtering: Packet filtering is a fundamental security measure that helps protect networks from unauthorized access. Firewalls and intrusion detection systems (IDS) use packet filtering to analyze incoming and outgoing traffic, allowing or blocking packets based on predefined rules. This helps prevent attacks and unauthorized access to sensitive data.
- Firewall Technologies: Firewalls are essential for maintaining network security. They can be hardware-based, software-based, or a combination of both. Modern firewalls often include advanced features such as stateful inspection, which tracks the state of active connections and makes decisions based on the context of the traffic.
- Encryption and Packet Protection: Encryption is a critical component of network security. By encoding data within packets, encryption ensures that even if packets are intercepted, the information remains secure. Common encryption protocols include SSL/TLS for web traffic and IPsec for securing IP packets. Implementing encryption helps protect sensitive information, such as passwords and personal data, from unauthorized access.
Challenges and Innovations of Network Packets
As technology advances, the challenges associated with network packets continue to evolve.
- Increasing Packet Sizes: The trend toward larger packet sizes is driven by the demand for high-definition content and large file transfers. This increase can lead to network congestion and performance issues. Network engineers must develop strategies to manage larger packets effectively, such as optimizing routing protocols and implementing Quality of Service (QoS) measures.
- High-Speed Networking: The push for higher internet speeds is reshaping the landscape of networking. Technologies such as fiber optics and 5G are enabling faster data transmission, but they also require new approaches to packet handling and routing. Network professionals must stay informed about emerging technologies and adapt their strategies to leverage these advancements.
- Internet of Things (IoT): The proliferation of IoT devices presents unique challenges for packet communication. With billions of devices connected to the internet, managing packet transmission and ensuring security becomes increasingly complex. Network architects must design scalable and secure networks that can accommodate the growing number of connected devices.
Conclusion
In conclusion, network packets are the backbone of digital communication, enabling the transfer of data across networks. Understanding their structure, types, transmission processes, and security considerations is essential for anyone interested in networking. As technology continues to evolve, the role of packets in global communication will only become more critical, shaping the future of how we connect and share information. By staying informed about the challenges and innovations in packets, we can better appreciate the complexities of the digital world we inhabit.
TRTC (Tencent Real-Time Communication) is a platform designed to facilitate real-time audio and video communication over the internet. To optimize network packets for effective communication, TRTC employs several strategies:
- Adaptive Bitrate Streaming: TRTC dynamically adjusts the bitrate of the audio and video streams based on the current network conditions. This ensures that the quality of the communication remains high even in fluctuating network environments, reducing packet loss and latency.
- Packet Prioritization: TRTC prioritizes critical packets, such as those containing audio and video data, over less important data. This helps ensure that essential communication is delivered promptly, minimizing delays and improving the overall user experience.
- Error Correction: TRTC implements advanced error correction techniques to recover lost packets. By using methods like Forward Error Correction (FEC), TRTC can reconstruct lost data without requiring retransmission, which is crucial for maintaining real-time communication.
- Network Quality Monitoring: TRTC continuously monitors network quality and adjusts its transmission parameters accordingly. This proactive approach allows the system to optimize packet transmission in real-time, ensuring smooth communication even in challenging network conditions.
Please feel free to Contact us or join us on Telegram or Discord.